Overview
Computer Forensics… What exactly does that mean?
It is the application of collecting and preserving electronic evidence via analysis and protocols ensuring the data is suitable for use in a court of law.
The practice of computer forensics began surfacing in the 1970s as law enforcement began to deal with cases such as financial fraud which involved computer systems. The explosion of computers in the workplace during the 1980s led to possibly the official birth of computer forensics with the creation of the FBI Magnetic Media program.
In the early 2000s we began to see the importance of digital data analysis spill over to the civil litigation landscape beginning with the Zubulake v UBS Warburg LLC case. Fast forward 15 years later and digital data is woven into the fabric of our lives and hiding in the dark corners of the internet. The need for computer forensics has never been greater.
Typically, computer forensics is used for data restoration, cybersecurity, law enforcement, and litigation. Forensic tools may enable a company to retrieve files originally assumed lost forever from a server’s hard drive or monitoring a network for intrusions. Law enforcement may image an entire computer to piece together the puzzle of evidence left at the “scene of the crime” during a criminal investigation. Finally, data may be forensically collected such as emails and corporate records to provide attorneys an easier way to find relevant documents during the discovery phase of a law suit.
It sounds daunting & scary but a forensic collection is nothing more than getting a copy of something that is exactly the same as the originating source. It’s as if someone was asked to hit the copy button on the photocopier. Of course, printing and copying all digital material is typically cost prohibitive, bad for the environment, extremely difficult to sift through when there are massive volumes of records, and we lose the ability to see the metadata.
Information Worldwide
Let’s dive a bit deeper into the electronic data growth worldwide.
Studies within the last few years have indicated that 90% of the entire world’s data has been generated recently and is all electronic. Web 3.0 connectivity, personal smartphones & tablets, and social media exponentially increase the amount of data being generated daily and only less than a quarter of this information is transient. Furthermore, it is estimated that at least “80% of all the data in the digital universe is the responsibility of enterprises”. John Gantz predicts that the digital universe doubles every two years until 2020 and there will be “5,200 gigabytes for every man, woman, and child in 2020.”
In 2012, Neil Spencer wrote: “To put things into perspective, this infographic by DOMO breaks down the amount of data generated on the Internet every minute. YouTube users upload 48 hours of video, Facebook users share 684,478 pieces of content, Instagram users share 3,600 new photos, and Tumblr sees 27,778 new posts published. These are sites many people around the world use on a regular basis, and will continue to use in the future. The global Internet population now represents 2.1 billion people, and with every website browsed, status shared, and photo uploaded, we leave a digital trail that continually grows the hulking mass of big data.”
The need for proper digital collection methods and search capabilities have never been more important.
Computer Forensics in Litigation
Okay, so there’s lots of electronic data out there but why is forensics involved in a legal matter
More and more legal cases involve digital data, more commonly referred to as Electronically Stored Information (ESI), which may include emails, text messages, spreadsheets, memos, or accounting records just to name a few. As mentioned before, Zubulake v UBS Warburg LLC helped define the role electronic information plays within legal matters and eventually led to amendments in the Federal Rules of Civil Procedure (FRCP) regarding ESI retention and management.
As the digital age moves forward, the amount of ESI being generated continues to grow exponentially requiring a systematic (& defensible) approach to collecting information that may be needed in litigation. ESI is so prevalent that in 2014 the California State Bar issued the Formal Opinion Interim No 11-0004 noting: “Not every litigated case ultimately involves e-discovery; however, in today’s technological world, almost every litigation matter potentially does. The chances are significant that a party or a witness in the matter has used email or other electronic communications, stores information digitally, and/or has other forms of ESI related to the dispute.”
In many cases, expert analysis of ESI is needed to either prove or defend against a claim of wrongdoing. A proper forensic collection provides an audit trail of a collection, proper chain of custody, and an exact copy or image of the data in question so a proper review can be conducted.
When Do You Forensically Collect?
Well, to know when to collect requires an understanding of how a legal matter begins, the rules surrounding material that should be collected, and the model devised to guide the industry on the proper methodology for finding, capturing, and reviewing ESI.
A lawsuit begins when the plaintiff files a complaint with the court outlining a suspicion of wrongdoing by one or more defendants. Thus begins a series of pre-trial processes one of which is defined by Rule 26(b)(1) under the Federal Rules of Civil Procedure allowing both parties to “obtain discovery regarding any non-privileged matter that is relevant to any party’s claim or defense.” This particular pre-trial process, commonly referred to as the Discovery Phase, has become the center of much debate within the legal community as the amount of ESI continues to rapidly grow causing major delays and increasing costs within civil litigation.
The Discovery Phase has become such an enormous undertaking that in 2005 an entire standardization model called the Electronic Discovery Reference Model (EDRM) www.edrm.net was defined for the industry. The EDRM contains 9 stages providing guidelines for properly managing the material and tasks associated with discovery. The Collection Phase appears nearly halfway into the EDRM in tandem with Preservation.
Proper forensic practices play a large role in the EDRM’s Collection phase though it is important to understand what has to be collected first.
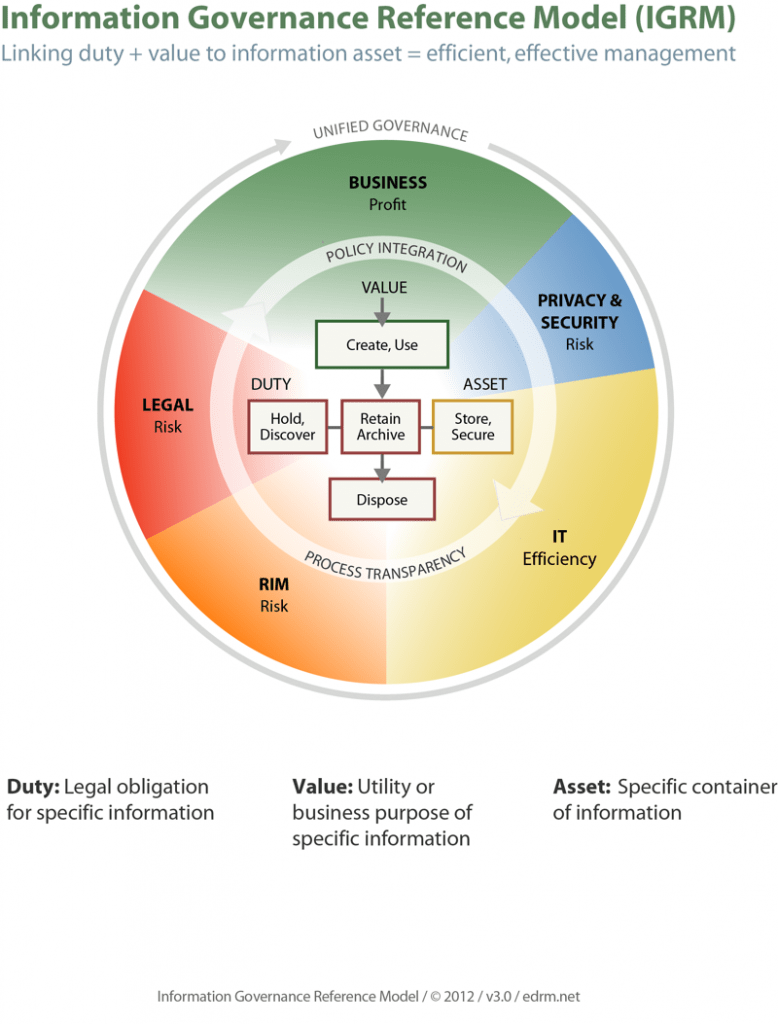
Inforation Governance
This phase is primarily centered around corporate information management policies. Bryan E. Hopkins, a former in-house lawyer for Samsung Electronics America Inc., appropriately points out in his book Legal Risk Management for In-House Counsel and Managers that the cost of discovery continues to grow and the lack of a proper information governance plan can be fatal for an organization if faced with litigation.
“The problem facing companies when dealing with ESI is that ESI-related technologies have become numerous and complex. The ability to local, retrieve, collect, review, and produce relevant ESI (Including e-mail) may determine a company’s future, once it is involved in litigation.
The reasons for this include:
- Some reports estimate that approximately 80 percent of costs of litigation are related to discovery, including E-discovery.
- Litigation involving E-discovery in the United States can be costly.
- Failure to have an adequate E-discovery process can be fatal.
- US Federal Rules of Civil Procedure and US case law (Zublake v UBS, etc.) have created significant issues and costs.”
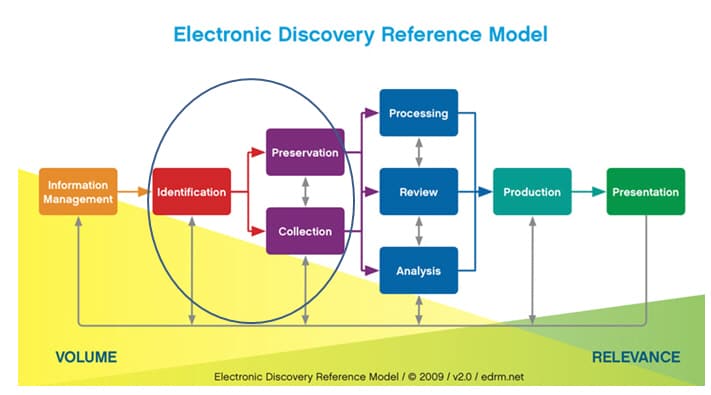 [click to view EDRM]
[click to view EDRM]Identification
Per the EDRM guide, “identification is used to identify potential sources of relevant information.” This particluar phase is essential to correctly identify the sources (business units, people, IT systems and paper files) of information that may be relevant to the matter even beyond ESI in order for a proper placement of a legal hold (Preservation).
“The [Federal] rules impose an obligation to identify data that is potentially relevant and reasonably accessible, as well as data that may be relevant but not accessible.” as stated by the CUA. Due diligence is a must within this phase to correctly identify all relevant parties, documents, and data. Furthermore, the ABA Standing Committee on Lawyers’ Professional Liability’s study “concludes that over 46 percent of malpractice claims are substantive-type errors” many of which occur within the realm of discovery.
Remembering the 5 P’s of success, Proper Planning Prevents Poor Performance, during this phase will help one avoid ethical violations, judicial sanctions, or a malpractice claim.
There are industry tools available to assist attorneys with identifying the proper sources for information within their client’s organization. These tools help implement legal holds and provide an audit trail of who, when, what, and what has been reviewed for relevance to the specific matter. Legal holds typically involve a written notice that is sent out across the organization or to a targeted group. This notice provides information around the matter and may require a response by all recipients to provide further details of document locations both physical and digital in order to preserve the material for review.
Preservation
EDRM.net suggests this phase in order to “promptly isolate and protect potentially relevant data in ways that are: legally defensible; reasonable; proportionate; efficient; auditable; broad but tailored; mitigate risks.”
This phase has become a hot topic in recent years due to motions for sanctions regarding the spoliation of ESI. Data spoliation refers to the process of altering, hiding, or deleting information relevant information to a matter whether it was negligent or intentional. The preservation phase provides guidelines for counsel, information officers, risk officers, and IT to defensibly safeguard all material. Here are some guidelines for preservation.
In 2010, the Federal Judicial Center performed a study and issued the Motions for Sanctions Based Upon Spoliation of Evidence in Civil Cases report. They determined that 40% of all motions for sanctions filed in 209 cases examined were related directly to ESI. Even as of writing this post, various courts such as the Supreme Court of Texas continue to clarify their understanding of spoliation and provide standards governing such.
Neglecting the duty to preserve is no longer an option and consistently maintaining the highest standard for this process is typically the safest as obligations for preservation vary between jurisdictions.
Collection
Whew… Now it’s time to collect the data.
The forensic collection phase kicks off to ensure data is collected and transferred from the originating source to the review setting once all the sources have been confirmed and any steps have been taken by organizations to preserve a potentiality relevant set of data.
Proper collection of the ESI can safeguard against disputes that may arise reading the authenticity of the data and provides an auditable and defensible record of how the data was obtained.
The are various forensic methods and tools that may be employed during this phase depending on the nature of the litigation. Some matters may only require a proper audit trail and forensic copy where other matters may require expert analysis on physical hard drives in order to determine file deletions. Though litigation requires varying levels of forensics they overarching theme is the same: apply standardized methods and protocols for collecting the information in order to establish a clear, auditable trail to ensure evidence is admissible.
Following the collection phase, there are various other stages such as review that requires attorneys to determine what documents are relevant, determining what information may be privileged such as attorney-client communications, and producing information to the other parties which complete the EDRM.
It is clear the universe of digital material continues to expand not only in size but in sources containing data. Will we every be able create elegant, automated and unified solution further upstream providing a streamlined method for risk management, information governance, and preservation making it easier and cost effective to collect from all sources within an organization?