Overwhelmed with technology? Not sure how to start discovery? Conducting discovery should be easy. So, let’s make it easy.
These four fundamental steps set the stage for a consistent and thorough process:
1) Identifying the facts;
2) Recognizing the missing pieces;
3) Interviewing the key players; and
4) Compiling the appropriate scope of data for analysis and review.
It is important to be mindful of this process to ensure proper identification of data even when discovery seems straightforward.
Here’s a story…
 My team and I were recently asked to assist with a matter where the initial collection had already been performed. Once involved, I learned there had never been a full exploration into where all the data lived or who may have known where it would be. Needless to say, this client paid heavily in identification, collection, processing, and review charges as the entire process had to be redone and expedited to meet a looming deadline.
My team and I were recently asked to assist with a matter where the initial collection had already been performed. Once involved, I learned there had never been a full exploration into where all the data lived or who may have known where it would be. Needless to say, this client paid heavily in identification, collection, processing, and review charges as the entire process had to be redone and expedited to meet a looming deadline.
The client had already delayed a production prior to us arriving and were unable to get an additional extension of time. Our team immediately identified the known facts and key players. We crafted a few questionnaires for the key people and then followed up with an over-the-phone interview.
We learned that numerous sources of data had been left untouched and were completely unknown prior to the questionnaires. A proper identification of data or a general understanding of the client’s digital infrastructure was nowhere to be found.
Of course, this could have easily gone the other way as well. Too much information could have been collected than was needed to respond.
Either type of error in misjudging a collection would be negligent and egregiously missing a few basic steps. Having a proper and defensible process in place helps avoid the pitfalls of performing data discovery.
Explosion of Data
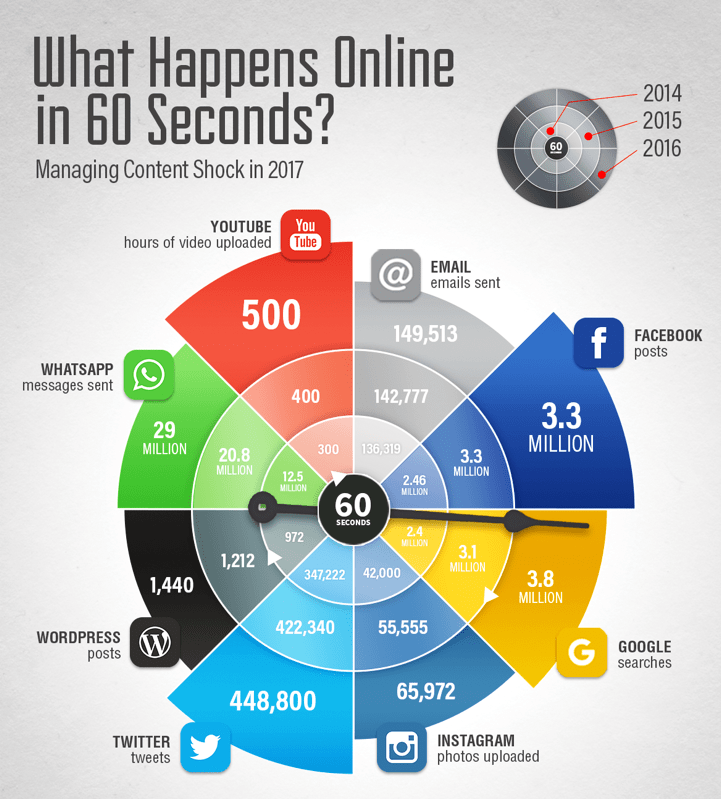
Over collection can be unnecessarily expensive for your client. Under collection can result in missing relevant data or worse, sanctions. Both of these are bad.
The explosion of data and sources doesn’t ease the fact-finding process. Knowing what type of information generally exists will help when crafting questions and creating the collection scope.
But…data is being produced at enormous rates minute-by-minute across many different types of gadgets.
Email is still one of strongest methods of business communication and one of the most voluminous. It’s estimated that 225 billion emails will be sent in 2017. Furthermore, 65% of those emails will be done via a mobile device!
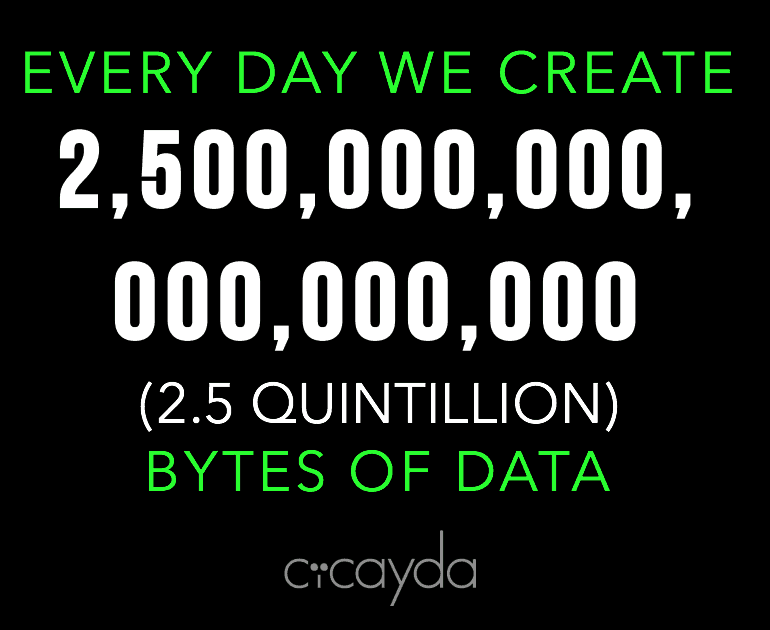 This increase of information means it’s easier than ever to over collect data or miss sources when gathering potentially relevant material for discovery purposes. 70% of the dollars spent in litigation is spent on discovery and data sizes are not in decline!
This increase of information means it’s easier than ever to over collect data or miss sources when gathering potentially relevant material for discovery purposes. 70% of the dollars spent in litigation is spent on discovery and data sizes are not in decline!
In 2014, Bloomberg BNA reported findings from a survey conducted throughout US based corporate counsels. Overwhelmingly, nearly half (48.4%) of counsels polled replied that “understanding the universe of potentially responsive evidence early in the case” was a major factor when considering their eDiscovery process.
We know it is inevitable that data volumes will constantly be on the rise; however, follow the steps to help minimize the relative scope of data.
Get back to the basics.
Proper attention to the fundamentals allows for a more concise collection regardless if discovery has an “E” in front of it or not. It also reduces unknown unknowns when preparing and allocating budgets and resources.
Taking time to prepare a discovery scope may also lead to additional questions and insights you find useful outside the linear “review-to-produce” process.
Legal discovery is a journey.
You wouldn’t walk out the door and hop on a plane without travel essentials. You’d think about what to pack, what bag to take, and did you get your toothbrush.
The same mental preparation and checklist applies to discovery.
Facts, just the facts.
Do you have solid understanding of the matter?
Could you draft a statement of facts?
Crafting a similar document allows you to outline the items you believe to be true, the material facts, and exposes the holes in the story. The missing items may warrant an entire list of questions to be sent to certain witnesses and/or establish a baseline for your Request for Production (RFP).
Confirm What You Know
Start by creating a formal interview and questionnaire plan.
It is critical to explore all avenues of communication methods and record keeping within this phase. Though there are numerous technology outlets for data to live, it isn’t much different than in was in the paper days.
Don’t let the changing world of technology
lead you astray from the process.
In the not so distant past, one would ask if any records or memos were stored offsite, kept in a briefcase, in an office drawer, or in the lateral files. These locations still may exist physically but they are also parallel today’s technology. Offsite is now the cloud, the briefcase is now the laptop, the office drawer is a flash drive, memos are emails, and so forth.
The importance of exploring all locations for data may be exemplified within a Trade Secret Theft matter. 
It’s commonplace to have competition in the capitalist environment, though no one wants to lose customers to the competitor because of stolen trade secrets. However, it is often common for a former employee to “take” with them valuable information regarding customer contacts, pricing programs, and contracts.
A Washington Post article, Data Theft Common By Departing Employees, notes: “nearly 60 percent of employees who quit a job or are asked to leave are stealing company data…Seventy-nine percent of those who admitted to taking data said they did so despite knowing that their former employer did not permit them to take internal company information”.
Summarily, SRGLaw proposes that “[v]irtually every employer doing business in America faces the threat of its own employees walking out the door and taking the company’s confidential information, business leads, clients and other core business assets with them”.
We know that more and more employees are using personal devices such as mobile phones to conduct business on behalf of their employer. Even with the most lenient non-complete agreements in place, many states are leaning more towards the right to work and it is highly unlikely your customer information will ever be removed from those personal items. As seen in cases such as Dowell v. Biosense Webster, Inc., the court ruled that the non-compete and non-solicitation clauses were “facially void” under California’s Business and Professions Code.
However, the blatant theft of corporate data such as entire contact lists stored within customer relationship management systems (CRM) is a different issue altogether and may violate the Computer Fraud and Abuse Act (CFAA).
Legal discovery is a journey.
Not fully understanding the type of CRM platform may overlook a key element when attempting to establish proof of the theft.
For instance, many cloud based CRM systems not only record user based logins to the system, but also record when a list is generated and the timestamp of any download. Having this information could be the critical information needed to pursue an injunction to be granted.
Establishing a through questionnaire, noting the type of CRM, the accessibility and logging of access, etcetera is critical not only as a discovery item but also as material fact of the case.
Facts Have Been Identified. What Now?
Start identifying your key witnesses once you have a foothold on the known facts and unknown items around the  case.
case.
These folks will be essential resources for confirming where the data lives, how to access it, and what source may be excluded. Keep in mind, some of these key people may also need to be called on as 30(b)(6) witnesses as well. Find out what they know!
The easiest way to start this process is through a notification and questionnaire.
- Identify who may or may not be essential for finding the facts and the data
- Determine if a single set of questions for all would be helpful or if individual/group based questionnaires would produce more informative results
- Prepare a formal Legal Hold Notice
Think about the job roles these key people have within the organization. Tailoring individual sets of questions for groups based on roles may result in better responses and provide an opportunity to reduce witnesses and/or hone in on more key facts.
Different Questions, Different Answers
By way of example, questions regarding methods of communication, policies, and document storage may be completely different when posed to executives versus those in the IT department.
Executives may be able to answer questions regarding their knowledge and involvement with XYZ topic. They may be able to respond as to how and with whom they communicated about XYZ. Finally, they may be able to recall where documents were saved such as their flash drives, desktop, or the infamous S: drive.
Most of these witnesses would not have a clue regarding the retention and backup policy for the company and whether or not this data is stored offsite. These are the types of questions more suited for the IT group.
Creating multiple, independent questionnaires greatly increases valid responses across different divisions. It also may assist with connecting the who, what, and where.
Define the Collection
It is time to define the scope of collection by piecing all of that information together.
This process is critical for proper identification of potentially relevant material and to determine volume.
A great example of why this process matters is In re A&M Florida Properties II. The plaintiff in this matter failed to identify the sources of data when a broad search was conducted. Consequently, some of the deleted data was overlooked, was not produced, and the plaintiff had to repeat numerous forensic searches within the company. “Under this court’s holding, attorneys have an obligation to go beyond simple requests to look for documents to ‘become fully familiar with [the] client’s document retention policies, as well as [the] client’s data retention architecture.’”
Second Nature
Starting discovery with a formal litigation discovery checklist should be second nature. Daniel Kaheman suggests that “[v]alid intuitions develop when experts have learned to recognize familiar elements in a new situation and to act in a manner that is appropriate to it.”
Don’t let the changing world of technology lead you astray from the process.
Stay steady and start with the foundational items every time! You can always loop in the techie folks, like me, who’s day-to-day job is keeping track of the evolving market.
Together we can establish a repeatable and defensible process for information gathering to avoid discovery overload.